Create and test DAST projects for web applications and APIs
To run dynamic tests on a web application or API, you first need to create a DAST project in Polaris. Configure some basic settings—including the entry-point URL, target type, and authentication method—and then create the DAST project and associated profile.
Prerequisites
Before you begin, make sure that:
- Your organization has a subscription with a DAST entitlement.
- You have permissions to create and manage projects.Note: See Roles and permissions for more information.
- Your subscription has at least one available DAST project.
- An Organization Admin or Organization Application Manager has either:
- Created an application that uses your DAST subscription. Note: See Create an application for more information.
- Assigned your DAST subscription to a preexisting application. Note: See Assign subscriptions to applications for more information.
- Created an application that uses your DAST subscription.
- Polaris has network access to the web application or API you want to scan (only required for external targets). To run DAST tests on external targets, Polaris communicates with your Internet-accessible applications or APIs using IPs that vary between Polaris instances.
Table 1. fAST Dynamic (DAST) IPs Polaris instance IPs (outbound) America, production - 192.231.134.0/24
America, POC European Union, production - 162.244.5.0/24
Kingdom of Saudi Arabia, production - If you want to start DAST tests directly from Black Duck Bridge or a CI/CD pipeline, Bridge CLI version 3.7.0 or later is required.
Additional prerequisites for scanning internal targets
Running DAST tests on internal web applications and APIs (inside private networks) is supported through the Secure Tunnel feature of the Black Duck Bridge. To use this functionality, you must install the Bridge CLI version 3.1.0 or later. For more details, see Test internal DAST projects with Polaris Secure Tunnel and Connect to an internal DAST target from the Bridge CLI in the Bridge CLI documentation.
Create a DAST project
- Web applications
- APIs
A target is identified by its Entry Point URL and can be Internet-accessible or internal (inside a private network). A separate DAST profile is needed for each target you want to scan using fAST Dynamic. A single DAST project can be used for testing a web application or an API target, but not both.
Create a DAST project for a web application target
Create a DAST project for an API target
Test a DAST project
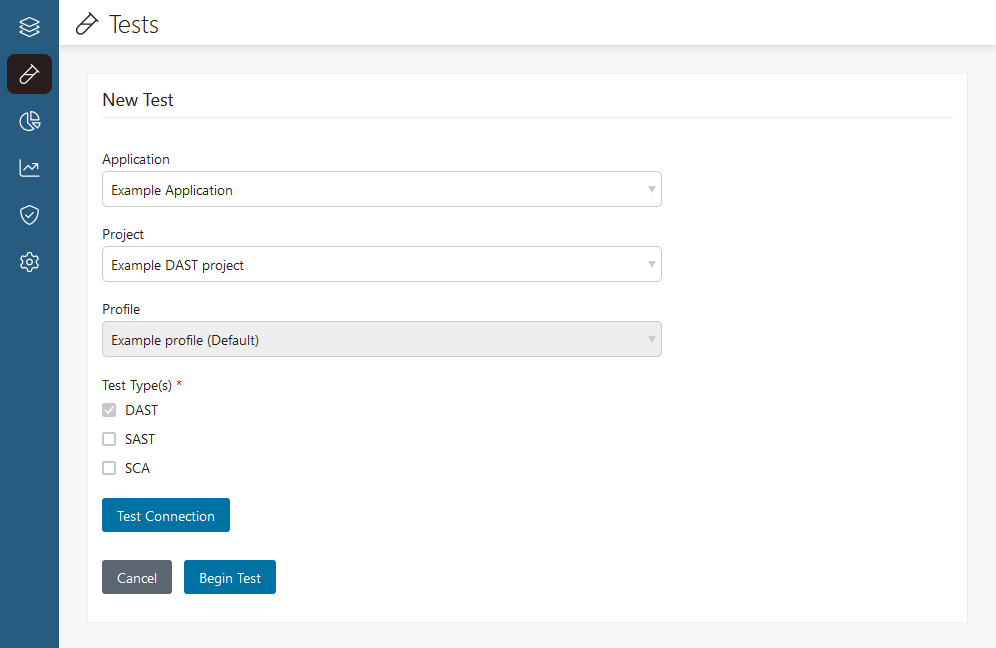
Follow these steps to run a DAST test from the Polaris user interface:
 | Dev Portal
| Dev Portal